When ThreatFire detects what it considers to be suspicious behavior on your computer, it alerts you with one of three types of alerts - the "Known Malware" alert, the "Potentially Malicious" alert, or the "Potentially Unwanted Application" alert.
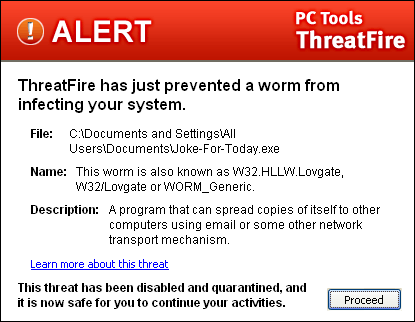
When ThreatFire detects an attack on your computer by a known threat, it will immediately terminate the attack and permanently isolate the malware process in quarantine. An alert screen will display and notify you that ThreatFire has prevented the attack.

All you need to do is click "Proceed" to get back to what you were doing at the time of the attack.
When ThreatFire detects a "potentially malicious process" that might be a virus attack, it will immediately suspend the suspicious process and alert you that your computer may be at risk:
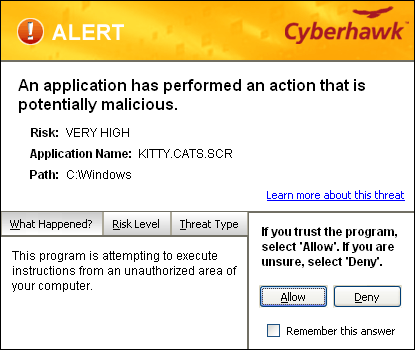
You have three courses of actions open to you. You can:
|
|
|
Let's say you have a trusted application that you recognize as the application that triggered the alert. In that situation, you could instruct ThreatFireto always allow the operation to proceed. If you change your mind, you can always Remove the item from the Allowed list in the Threat Control Center to reverse your decision.
Click the "Learn more about this threat" link to launch a quick web search on the threat. In most cases the result of this search provides a clear indication of how to proceed.
Some applications are not clearly good or clearly bad, but may fall somewhere in between as ôgrayware.ö ThreatFire refers to these programs as ôPotentially Unwanted Applicationsö or PUAs. PUAs can include adware or system administrator tools or other classes of programs. When ThreatFire detects that a PUA is attempting to run on your computer, it will immediately halt the process and notify you with the following alert:
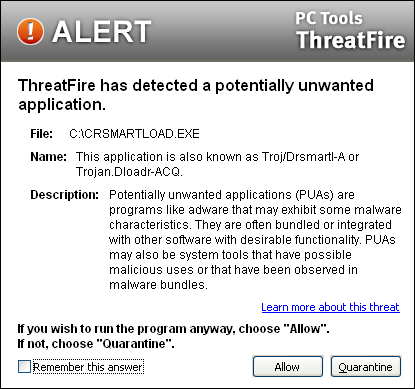
You have three courses of actions open to you. You can:
|
|
|
While all adware is designed to serve you ads in some format, it is sometimes bundled with other software programs that you may actually want. It is completely your choice whether to run a PUA or not. Let's say you have a trusted application that you recognize as the application that triggered the alert. In that situation, you could instruct Cyberhawk to always allow the operation to proceed. If you change your mind, you can always Remove the item from the Allowed list in the Threat Control Center to reverse your decision.
Click the "Learn more about this threat" link to launch a quick web search on the threat. In most cases the result of this search provides a clear indication of how to proceed.